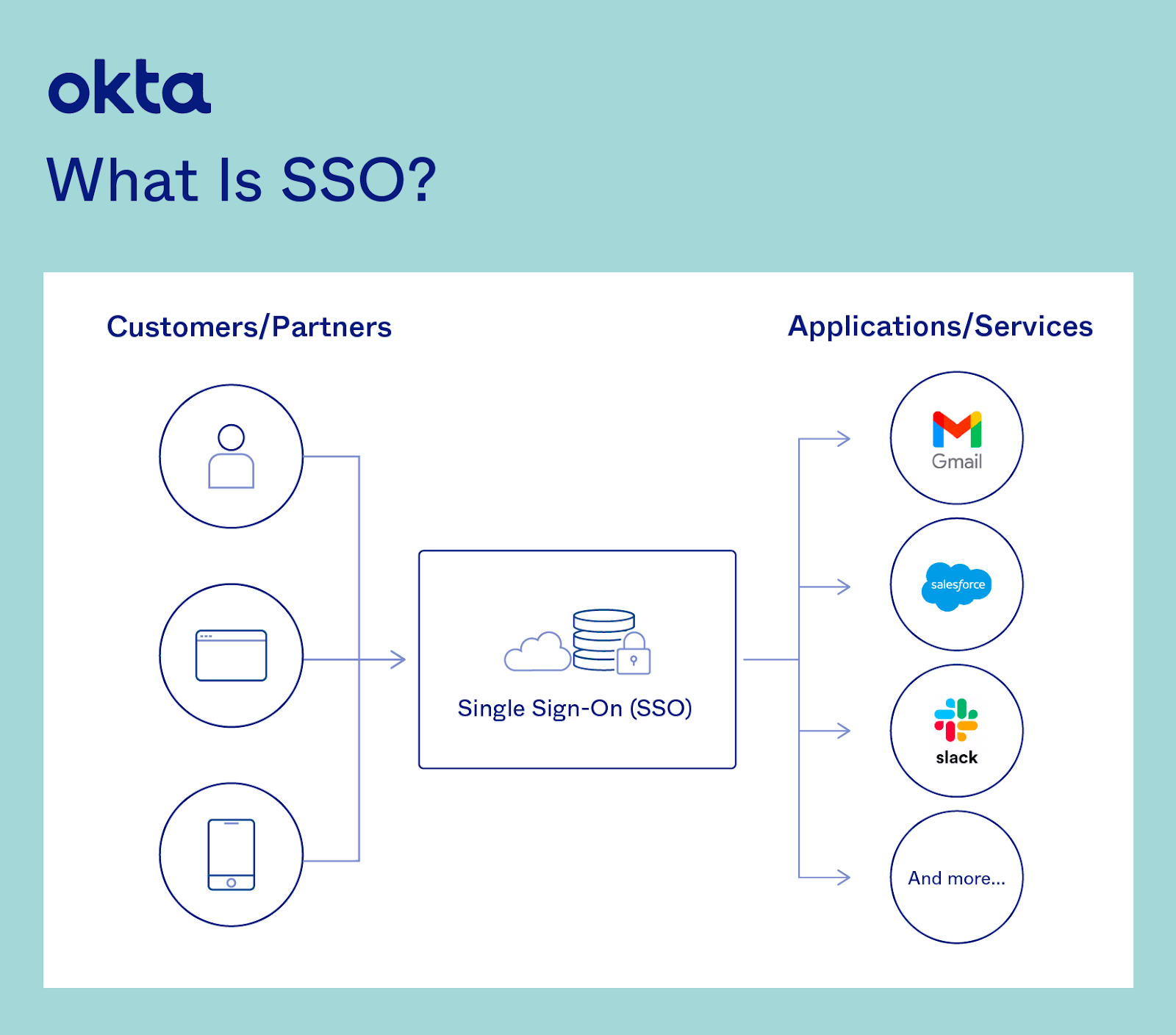
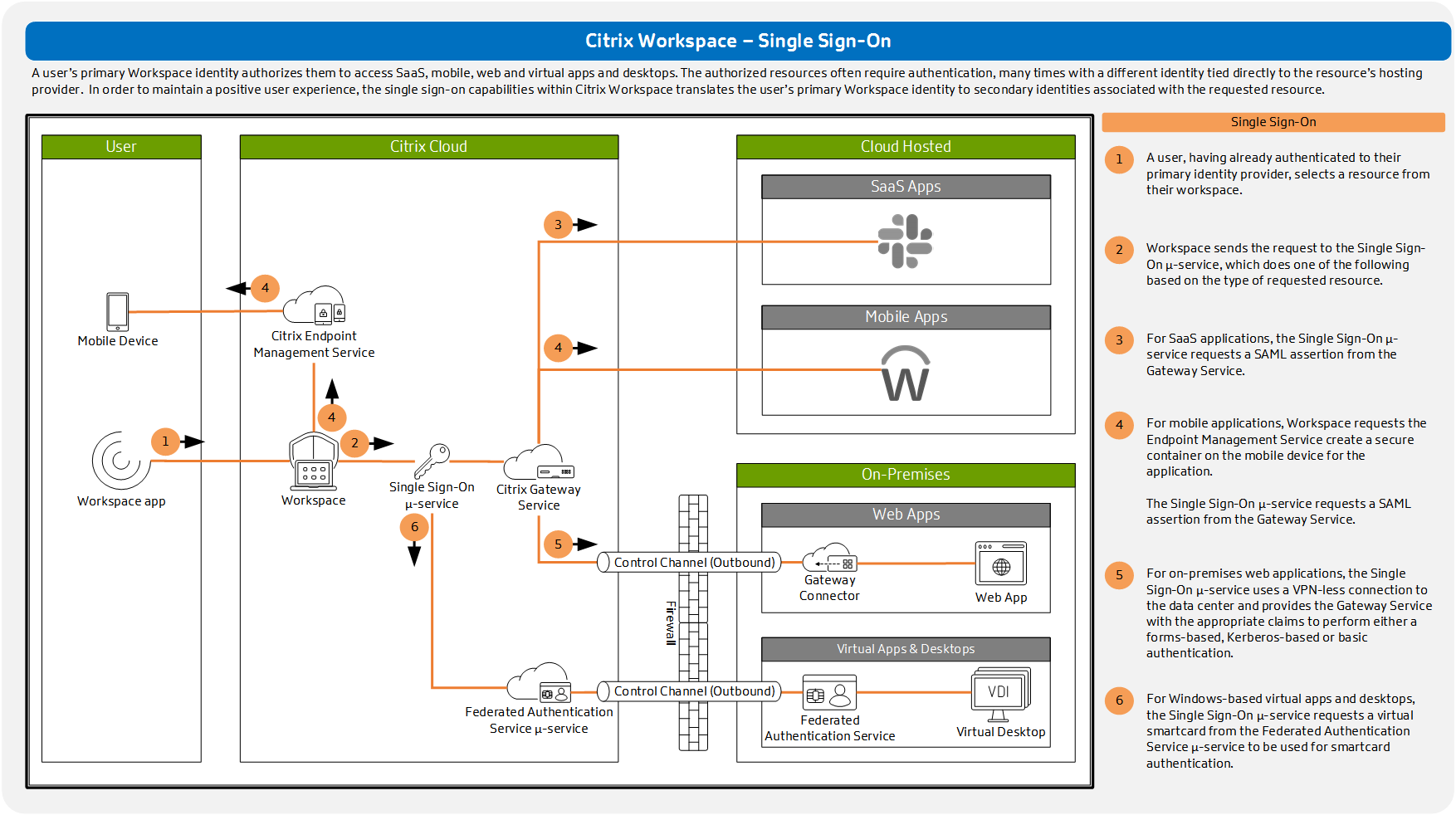
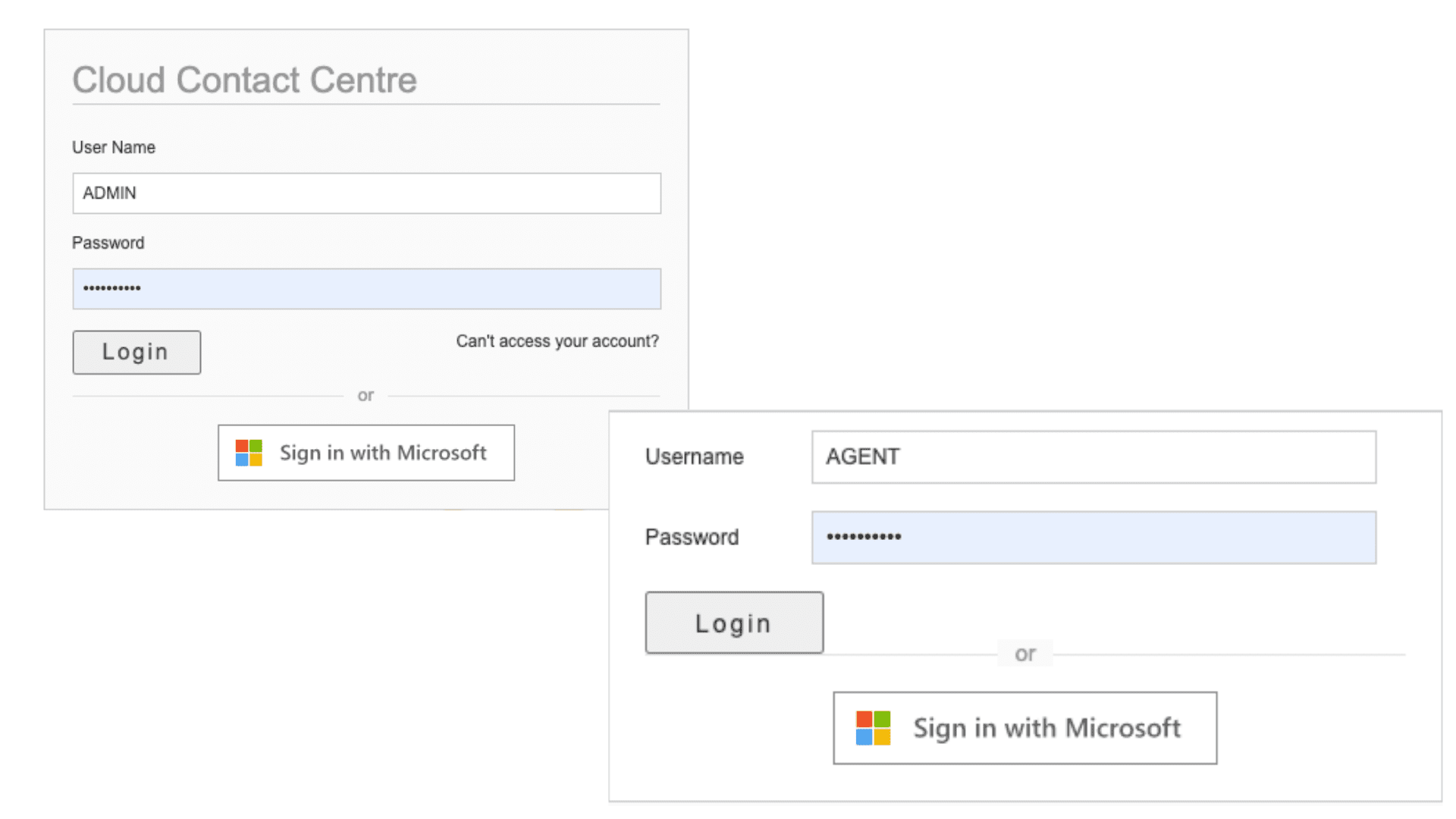
Single-Sign-On (SSO) capabilities with Identity Providers | by Dinuwan Kalubowila | Microsoft Student Champs — Sri Lanka | Medium
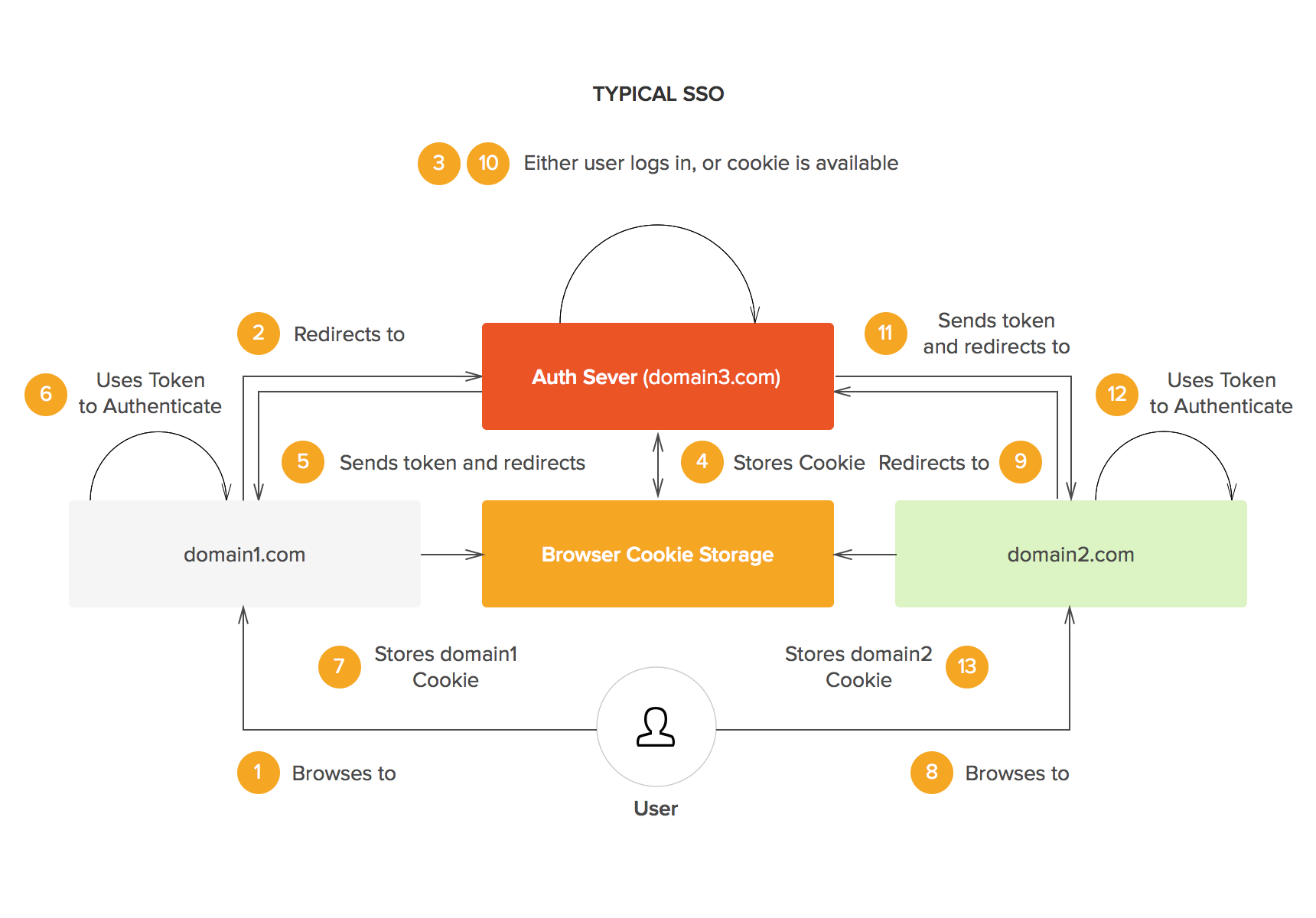
Single Sign-On(SSO) -SAML Authentication Explained | by Prakhar Jain | Connected Lab TechBlog | Medium

Operation models of single sign-on (SSO) protocols (logical flows) in... | Download Scientific Diagram